Digital Marketing Executive
24.01.25
LIMA teams up with UA92 to boost Linux skills
04.03.25
In 2025, IT teams are tasked with the increasingly complex task of managing cybersecurity requirements alongside an ever-growing list of responsibilities.
Organisations are striving to improve their security posture, while driving awareness of security issues internally, and ensuring end users are using systems and data securely.
Proactive teams monitor and audit IT systems to detect early signs of compromise, but time and resources are not on their side.
Day-to-day IT support is still the main occupier of time, with more than 59% of IT teams spending most of their time on IT support. The 9am rush of phone calls about password resets, software issues and trapped emails is still very real.
Meanwhile, time spent on protecting against security threats is just 16%, much of which is swallowed up delivering patches, workarounds and fixes within CE+ timeframes.
Without the time to dedicate to proactive security activities, a lack of regular and reliable visibility of external vulnerabilities leads to increased cyber risk.
Amidst all of this, annual penetration testing remains a staple of the IT and security team’s toolkit.
Why do we penetration test?
- Conducting annual security tests is considered good practice in the industry. Regular testing can help to ensure security measures are up-to-date and effective.
- Standards like PCI DSS (Payment Card Industry Data Security Standard) mandate annual security assessments to protect cardholder data.
- Testing may help you to meet and evidence the requirements of other frameworks including GDPR and ISO 27001.
- Annual security tests provide external validation of your security posture. This can help to build trust with stakeholders, including customers, partners and regulators.
- Many cyber insurance policies require regular security assessments to prove proactive management of security risks. By performing annual tests, you can meet these requirements and potentially benefit from lower premiums or better coverage terms.
- Many customers and suppliers expect partners to have strong security practices in place. Annual security tests can be a requirement in contracts or service level agreements.
Four ways to get the most out of your annual test
While penetration tests remain an important part of many organisations’ security strategy, there are several areas in which they fall short. By having an awareness of the trusty pen test’s shortcomings, you can make sure you’re effectively filling the gaps and maximising the return on your security investment.
1. Use your test as a benchmark
Annual security testing provides a snapshot of your system’s security posture at a specific point in time. While you may make improvements based on the test results, new vulnerabilities can be introduced through subsequent changes or configurations. While your annual test is a useful benchmark, your security status can quickly become outdated, leaving your system exposed to new threats that arise after the test.
2. Be aware that your environment constantly evolves
Annual tests might not capture the dynamic nature of your IT environment. Systems, applications and networks are constantly evolving, and new vulnerabilities can emerge at any time. Relying solely on annual testing can give a false sense of security, as it may not account for changes or new threats that occur between tests.
3. Be very clear about what needs to be in scope
Security tests are often scoped to focus on specific areas or components of your environment. If certain systems or applications are excluded from the scope, potential vulnerabilities in those areas may go undetected. This can leave significant parts of your infrastructure unprotected and vulnerable to attack. If you miss an element from your annual test, it’s usually tricky and/or expensive to re-run it with an amended scope.
4. Fill in the gap in your testing cycle
Cyber incidents can occur at any time, and the average timescale for detecting and responding to these incidents is often much shorter than your testing cycle. Annual testing does not provide the continuous monitoring needed to detect and respond to threats in real-time. This misalignment can result in delayed detection and response, increasing the risk of a successful attack. Have a plan for filling the gap.
How can you fill the gap left by annual testing?
Annual testing falls short because it’s static, it’s unresponsive to change and it allows a huge window of time for vulnerabilities to be introduced and exploited. The lifecycle of a security breach is less than an annual testing cycle.
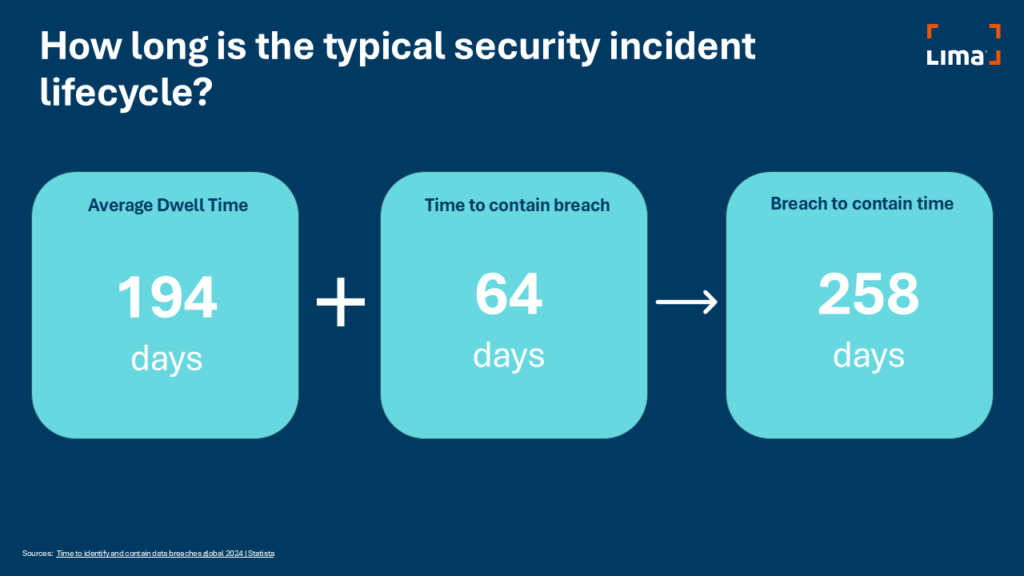
LIMA has developed a solution to perfectly complement, and in some cases replace, your annual security test.
Vulnerability Detection and Remediation (VDR) from LIMA uses a combination of software and human intervention to review your environment, reveal vulnerabilities and resolve them within an SLA that’s aligned to Cyber Essentials Plus.
By using VDR you can remove the risks presented by your annual test and free up the time and resources taken up by the constant demands of patching within your IT team.
1. Use your test as a benchmark
Because the average lifecycle of a vulnerability and its eventual exploitation is within your annual security test timeframe, we need to reduce window.
One of the key motivations to test more frequently is for the purpose of retesting, which involves running the same tests again after remediation to confirm that any fix has been successful. Even simple errors, like forgetting to reboot after applying a patch, can cause a vulnerability to persist.
With VDR, changes and developments in your environment are reviewed on a continuous basis. The service spots vulnerabilities and remediates them against an SLA aligned with Cyber Essentials requirements.
2. Be aware that your environment constantly evolves
VDR gives a picture of your environment, with no changes required to allow access – which is often a requirement of penetration testing. In fact, we recommend you keep everything as it is on a day-to-day basis so we get a full and accurate view, and we can see what layer of your stack is compromised or at risk.
3. Be very clear about what needs to be in scope
With asset-based pricing, you select the assets that you want to be covered by the scan. These can change and flex on a monthly basis in response to shifting requirements.
4. Fill in the gap in your testing cycle
VDR scans are run near-continuously, and when we spot a vulnerability, we address it within the SLA window, comfortably beating the average lifecycle of a vulnerability and filling the gap left behind by annual testing.
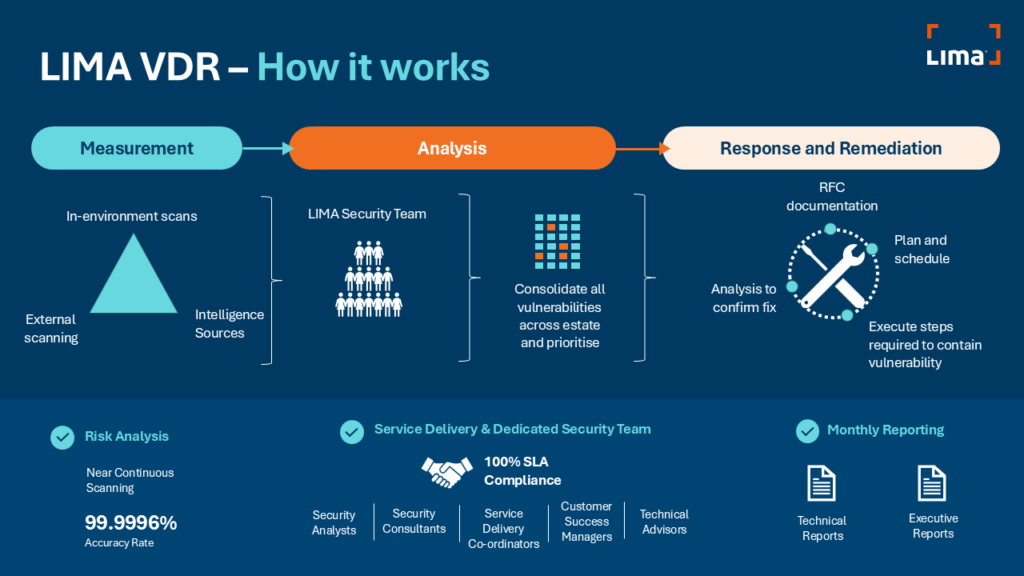
VDR continuously scans your environment for vulnerabilities and resolves them before they can be exploited, keeping you ahead of the game in the fight against cybercrime.
Want to remove the cyber-strain from your IT team? Contact one of our experts on 0345 345 1110 to discuss your free cyber-readiness assessment, or drop us an email: enquiries@lima.co.uk


